Error Generating Dh Server Key Exchange
- Error Generating Dh Server Key Exchange 2017
- Error Generating Dh Server Key Exchange Rate
- Error Generating Dh Server Key Exchange Rate
- Error Generating Dh Server Key Exchange Handshake Message
- Error Generating Dh Server Key Exchange Calculator
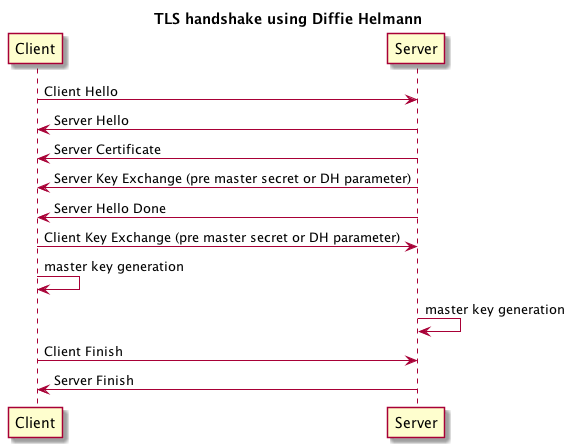
This indicates that the site is defaulting to an obsolete encryption cipher which is vulnerable to the 'Logjam' attack that was in the news earlier this year. Error: 'java.lang.RuntimeException: Could not generate DH keypair'. Answer / Solution: This issue is caused by a dependency on the old TLS 1.0 protocol in the Java Runtime Environment (JRE) version that is used by the KFS 4.1 Database Utility, which uses a Diffie-Hellman key length that is no longer supported by Windows. It's not the number of bits in your key; it's the number of bits used to generate ephemeral keys, which is independent of the bit-length of your key. The ephemeral keys are used to achieve perfect forward secrecy, but it's not very perfect if they can be broken. – Mike Scott Sep 10 '15 at 15:24.
Error Generating Dh Server Key Exchange 2017
In some cases, such as when SSL certificate not correctly installed on the server, following warning message will appear in the browser: an error has occurred while connecting to www.site.com. SSL received a weak ephemeral key Diffie-Hellman in the handshake message 'Exchange keys server.' (Error code: ssl_error_weak_server_ephemeral_dh_key).
- The page you are trying to open cannot be shown because the authenticity of the received data could not be verified.
- Please contact website owners to advise them of this issue.
The reason behind this problem is that the server tries to establish a secure connection using a weak encryption key (less than 1024 bits). The recommended size of the encryption key is 2048 bits. The easiest way to generate this kind of improved encryption key is to use OpenSSL:
Openssl dhparam -out dhparams.pem 2048
To solve issue with different servers, you need to follow below steps:
- Specify secure cipher sets
- Define the appropriate parameters for the Diffie-Hellman algorithm
Solution for Apache:
SSL parameters can be globally defined in the httpd.conf file or in specific virtual hosts.
Cipher sets
Disable SSLv2 and SSLv3 support and enable TLS support by explicitly allowing / disabling certain ciphers in the specified order:
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
SSLHonorCipherOrder on
Diffie-Hellman parameters:
In recent versions of Apache (2.4.8 and higher), as well as OpenSSL 1.0.2 and later, you can directly specify a file with Diffie-Hellman parameters:
SSLOpenSSLConfCmd DHParameters '{path to dhparams.pem}'
If you use Apache with LibreSSL or work with versions of Apache 2.4.7 or OpenSSL 0.9.8a or later, you can add the Diffie-Hellman parameters generated earlier to the end of your certificate file.
Perform the config reset:
Sudo service apache2 reload
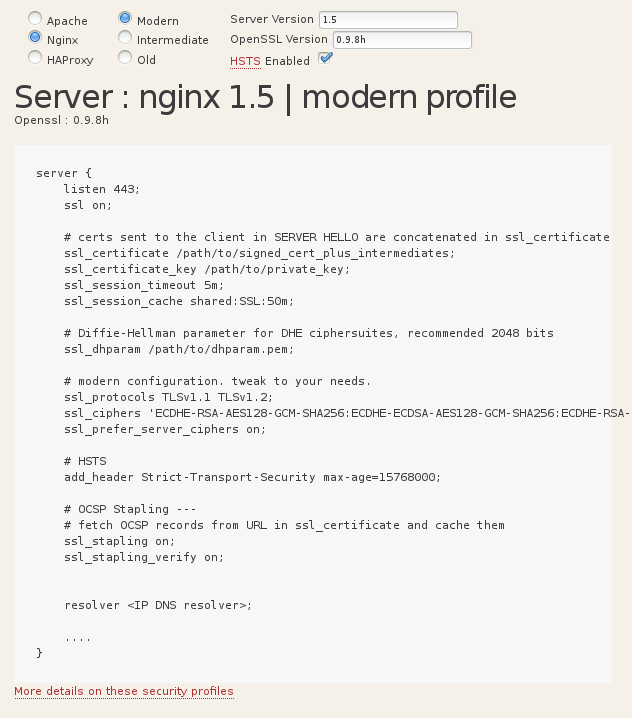
The solution for Nginx
In the server block in the site config (/etc/nginx/sites-enabled/default) add the following:
Cipher sets:
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
ssl_prefer_server_ciphers on;
Diffie-Hellman parameters
Ssl_dhparam {path to dhparams.pem}
Reload config:
Sudo nginx -s reload
Microsoft IIS
1. Open Group Policy Object Editor (run gpedit.msc in the command line).
2. Go to Computer Configuration, Administrative Templates, Network, and then click on SSL Configuration Settings.
3. In the SSL Configuration Settings section, open the SSL Cipher Suite Order parameter
4. Set stable ciphers. The list of ciphers can be reviewed on the Microsoft website or on the Mozilla page.
Lighttpd
Changes are made to /etc/lighttpd/lighttpd.conf.
Cipher sets:
/generate-key-csr-on-application.html. ssl.cipher-list = 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA '
Diffie-Hellman parameters
Ssl.dh-file = '{path to dhparams.pem}'
Reset config:
Sudo service lighttpd restart
Apache Tomcat
In the server.xml file (for JSSE)
Cipher sets:
<Connector
ciphers='TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_DHE_DSS_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_128_SHA256,TLS_ECDHE_ECDSA_WITH_AES_128_SHA256,TLS_ECDHE_RSA_WITH_AES_128_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_SHA,TLS_ECDHE_RSA_WITH_AES_256_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_SHA384,TLS_ECDHE_RSA_WITH_AES_256_SHA,TLS_ECDHE_ECDSA_WITH_AES_256_SHA,TLS_DHE_RSA_WITH_AES_128_SHA256,TLS_DHE_RSA_WITH_AES_128_SHA,TLS_DHE_DSS_WITH_AES_128_SHA256,TLS_DHE_RSA_WITH_AES_256_SHA256,TLS_DHE_DSS_WITH_AES_256_SHA,TLS_DHE_RSA_WITH_AES_256_SHA'
/>
Note: To use AES 256-bit ciphers, you must install JCE Unlimited Strength Jurisdiction Policy Files. You may find it at the following link.
Postfix SMTP
Both parameters must be specified in /etc/postfix/main.cf.
Cipher sets:
smtpd_tls_exclude_ciphers = aNULL, eNULL, EXPORT, DES, RC4, MD5, PSK, aECDH, EDH-DSS-DES-CBC3-SHA, EDH-RSA-DES-CBC3-SHA, KRB5-DES, CBC3-SHA
Diffie-Hellman parameters
smtpd_tls_dh1024_param_file = ${config_directory}/dhparams.pem
Reset config:
sudo postfix reload
Sendmail
Changes can be made in the LOCAL_CONFIG section of the file /etc/mail/sendmail.mc
Cipher sets:
O CipherList=ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
Diffie-Hellman parameters
O DHParameters={path to dhparams.pem}
Reset config:
sudo service sendmail restart
Dovecot
Changes can be made to /etc/dovecot.conf
Cipher sets:
ssl_cipher_list=ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
ssl_prefer_server_ciphers = yes (Dovecot 2.2.6 or greater)
Diffie-Hellman parameters:
#regenerates every week
ssl_dh_parameters_length = 2048
Reset config:
sudo doveadm reload
Error Generating Dh Server Key Exchange Rate
HAProxy
Changes are made to the global section of the config.
Cipher sets:
ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
Diffie-Hellman parameters:
Add to the bottom of .crt file with the Diffie-Hellman parameter generated with OpenSSL.
Note: despite the tune.ssl.default-dh-param option, which allows you to specify the maximum size of prime numbers used for DHE, placing arbitrary parameters in your certificate file will overwrite these values.
Reset config:
sudo haproxy -f haproxy.cfg -p $(</var/run/haproxy-private.pid) -st $(</var/run/haproxy-private.pid)
Amazon Elastic Load Balancing
The last set of predefined SSL parameters (2015-05) uses ECDHE ciphers, not DHE, which are resistant to LogJam attack. Details can be found in the documentation.
OpenSSH
The SSH protocol is protected from LogJam attacks, when an attacker can switch a connection to a weaker cryptography. However, many SSH implementations, including OpenSSH, use prime numbers, for instance 1024-bit Oakley Group 2. However, there are several ways to resolve this issue. The first and simplest method is to get customers to use the Diffie-Hellman algorithm on elliptical curves. In particular, Curve 25519. You can do this by setting Key Exchange algorithms:
KexAlgorithms curve25519-sha256@libssh.org
If you want to continue supporting the non-Elliptic Diffie-Hellman algorithm, you must disable Group 1 support by removing diffie-hellman-group1-sha1. You can leave diffie-hellman-group14-sha1, which uses 2038-bit prime numbers.
You can also generate new Diffie-Hellman groups:
ssh-keygen -G moduli-2048.candidates -b 2048
ssh-keygen -T moduli-2048 -f moduli-2048.candidates
You will then need to install the moduli-2048 in your system moduli file. In Debian / Ubuntu, it is located in /etc/ssh/moduli. SSH selects (in a random way) the groups from this file, so you must add new generated groups to the moduli file with removing the old ones.
Should you have any follow up questions or concerns, please feel free to contact LeaderTelecom support team using contact information provided on the website.
SSL_CTX_set_tmp_dh_callback, SSL_CTX_set_tmp_dh, SSL_set_tmp_dh_callback, SSL_set_tmp_dh - handle DH keys for ephemeral key exchange
SSL_CTX_set_tmp_dh_callback() sets the callback function for ctx to beused when a DH parameters are required to tmp_dh_callback.The callback is inherited by all ssl objects created from ctx.
SSL_CTX_set_tmp_dh() sets DH parameters to be used to be dh.The key is inherited by all ssl objects created from ctx.
Error Generating Dh Server Key Exchange Rate
SSL_set_tmp_dh_callback() sets the callback only for ssl.
SSL_set_tmp_dh() sets the parameters only for ssl.
These functions apply to SSL/TLS servers only.
When using a cipher with RSA authentication, an ephemeral DH key exchangecan take place. Ciphers with DSA keys always use ephemeral DH keys as well.In these cases, the session data are negotiated using theephemeral/temporary DH key and the key supplied and certifiedby the certificate chain is only used for signing.Anonymous ciphers (without a permanent server key) also use ephemeral DH keys.
Using ephemeral DH key exchange yields forward secrecy, as the connectioncan only be decrypted, when the DH key is known. By generating a temporaryDH key inside the server application that is lost when the applicationis left, it becomes impossible for an attacker to decrypt past sessions,even if he gets hold of the normal (certified) key, as this key wasonly used for signing.
In order to perform a DH key exchange the server must use a DH group(DH parameters) and generate a DH key.The server will always generate a new DH key during the negotiationif either the DH parameters are supplied via callback or theSSL_OP_SINGLE_DH_USE option of SSL_CTX_set_options(3) is set (or both).It will immediately create a DH key if DH parameters are supplied viaSSL_CTX_set_tmp_dh() and SSL_OP_SINGLE_DH_USE is not set.In this case,it may happen that a key is generated on initialization without laterbeing needed, while on the other hand the computer time during thenegotiation is being saved.
If 'strong' primes were used to generate the DH parameters, it is not strictlynecessary to generate a new key for each handshake but it does improve forwardsecrecy. If it is not assured, that 'strong' primes were used (see especiallythe section about DSA parameters below), SSL_OP_SINGLE_DH_USE must be usedin order to prevent small subgroup attacks. Always using SSL_OP_SINGLE_DH_USEhas an impact on the computer time needed during negotiation, but it is notvery large, so application authors/users should consider to always enablethis option.The option is required to implement perfect forward secrecy (PFS).
As generating DH parameters is extremely time consuming, an applicationshould not generate the parameters on the fly but supply the parameters.DH parameters can be reused, as the actual key is newly generated duringthe negotiation. The risk in reusing DH parameters is that an attackermay specialize on a very often used DH group. Applications should thereforegenerate their own DH parameters during the installation process using theopenssl dhparam application. In order to reduce the computertime needed for this generation, it is possible to use DSA parametersinstead (see dhparam), but in this case SSL_OP_SINGLE_DH_USEis mandatory.
Application authors may compile in DH parameters. https://treeprice248.weebly.com/blog/amtlibframework-mac-cs6-download. Files dh512.pem,dh1024.pem, dh2048.pem, and dh4096.pem in the 'apps' directory of currentversion of the OpenSSL distribution contain the 'SKIP' DH parameters,which use safe primes and were generated verifiably pseudo-randomly.These files can be converted into C code using the -C option of thedhparam application.Authors may also generate their own set of parameters usingdhparam, but a user may not be sure how the parameters weregenerated. The generation of DH parameters during installation is thereforerecommended.
An application may either directly specify the DH parameters orcan supply the DH parameters via a callback function. The callback approachhas the advantage, that the callback may supply DH parameters for differentkey lengths.
Error Generating Dh Server Key Exchange Handshake Message
The tmp_dh_callback is called with the keylength needed andthe is_export information. The is_export flag is set, when theephemeral DH key exchange is performed with an export cipher.
Handle DH parameters for key lengths of 512 and 1024 bits. (Error handlingpartly left out.)
SSL_CTX_set_tmp_dh_callback() and SSL_set_tmp_dh_callback() do not returndiagnostic output.
SSL_CTX_set_tmp_dh() and SSL_set_tmp_dh() do return 1 on success and 0on failure. Check the error queue to find out the reason of failure.
Error Generating Dh Server Key Exchange Calculator
ssl, SSL_CTX_set_cipher_list,SSL_CTX_set_tmp_rsa_callback,SSL_CTX_set_options,ciphers, dhparam