128 Bit Encryption Key Generator
- 256 Bit Encryption Key Generator
- 128 Bit Encryption Key Generator Review
- 128 Bit Encryption Key Generator Reviews
- Wep 128 Bit Encryption Key Generator
About the WLAN Key Generator
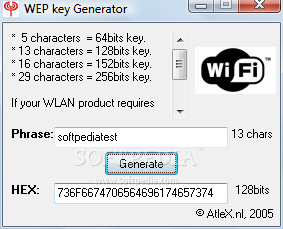
The SG WLAN Key Generator is a tool that allows for quick, valid, and strong WEP/WPA key generation. It uses the 94 standard ASCII characters (with codes 32 to 126) for maximum compatability.
To generate a random WEP or WPA key, simply choose the desired key length and one will be generated for you. To generate a key based on a custom passphrase, enter your phrase into either the Custom Key text fields, and its HEX or ASCII equivalent will be generated for you automatically in the other custom text field.
To use any of the generated WEP keys, simply right-click on the appropriate text field (highlight the text if necessary), then choose copy from the pull-down menu, and paste the text whesre applicable.
256 Bit Encryption Key Generator
Notes: WEP encryption uses 24 bit 'Initilization Vector' in addition to the 'secret key'. Therefore, 40 bit WEP can be refered to as 64 bit WEP, and 104 bit can be referedo to as 128 bit, depending on whether the 'initialization vector' is counted or not.
128-bit encryption is a data/file encryption technique that uses a 128-bit key to encrypt and decrypt data or files. It is one of the most secure encryption methods used in most modern encryption algorithms and technologies. 128-bit encryption is considered to be logically unbreakable. AES Example - Input (128 bit key and message) Key in English: Thats my Kung Fu (16 ASCII characters, 1 byte each) Translation into Hex: T h a t s m y K u n g F u.
For instance, if your WAP allows 64-bit encryption, you may or may not be able to use a FULL 64 bits. If that manufacturer uses the 24-bit internal trigger key, you may only be able to use a 40-bit entry. That is technically called 64-bit BASE encryption. For many of the encryption depths, we. Generate a random 128-bit key (k1), a random 128-bit IV, and a random salt (64 bits is probably sufficient). Use PBKDF2 to generate a 256-bit key from your password and the salt, then split that into two 128-bit keys (k2, k3). Make sure your algorithm's native output is at least 256 bits, or this will be slow. PBKDF2-SHA256 is a good choice. In a above post they are using 128 bit key value. I want to use my own key instead of hard coding the 128 bit key value. My question is that can I convert any random string into 128 bit key value. Please post some examples if it is possible to convert any string into 128 bit value.
128 Bit Encryption Key Generator Review
Create a WEP Key. This tool generate a WEP encryption key that you can use to secure your Wireless network. Generate the WEP Encryption key, copy it and paste it into your wireless router's configuration panel. Restart your DSL modem/router. Check the WPA Key Generator. AES Key Generator Devon 2019-04-27T15:14:21-07:00 Below is a Base64 Encoded AES-256 key which was been generated using the secure javax KeyGenerator. This key will work perfectly with any of the AES encryption code elsewhere on my site, and probably most of yours as well.
128 Bit Encryption Key Generator Reviews
Related Tools:- Security Scanner » Ports Database » Vulnerable Ports » Commonly Open Ports
128-bit Encryption
Last Post: May 9, 2010:
Wep 128 Bit Encryption Key Generator
OK, I've already forgotten some basics here!! Linksys wireless router specs say they support up to 128-bit encryption using WPA2. Somebody remind me why we have a 256-bit PSK, and how this relates to a 128-bit key?
WPA2 AES encryption uses two keys : PTK nad GTK, each 128 bit long.
Vertigo
This is an extract from
<sup>
AES is a block cipher, a type of symmetric key cipher that uses groups of bits of a fixed length - called blocks. A symmetric key cipher is a cipher that uses the same key for both encryption and decryption. The word cipher is used in cryptography to describe the instructions or algorithm used for encrypting and decrypting information.
With AES, bits are encrypted in blocks of plaintext that are calculated independently, rather than a key stream acting across a plaintext data input stream. AES has a block size of 128 bits with 3 possible key lengths 128, 192 and 256 bits as specified in the AES standard. For the WPA2/802.11i implementation of AES, a 128 bit key length is used. AES encryption includes 4 stages that make up one round. Each round is then iterated 10, 12 or 14 times depending upon the bit-key size. For the WPA2/802.11i implementation of AES, each round is iterated 10 times.
AES uses the Counter-Mode/CBC-Mac Protocol (CCMP). CCM is a new mode of operation for a block cipher that enables a single key to be used for both encryption and authentication. The 2 underlying modes employed in CCM include Counter mode (CTR) that achieves data encryption and Cipher Block Chaining Message Authentication Code (CBC-MAC) to provide data integrity.
CBC-MAC is used to generate an authentication component as a result of the encryption process. This is different from prior MIC implementations, in which a separate algorithm for integrity check is required. To further enhance its advanced encryption capabilities, AES uses a 48-bit Initialization Vector (IV). AES has no known attacks and the current analysis indicates that it takes 2<sup>120 operations to break an AES key—making it an extremely secure cryptographic algorithm. </sup>
</sup>
I will correct myself and explain AES-128 (CCMP) and GTK derivation steps in 802.11i standard
1. Pairwise Master Key (PMK) = TLS-PRF(MasterKey, “client EAP encryption” clientHello.random serverHello.random)
2. Pairwise Transient Key (PTK) = EAPoL-PRF(PMK, AP Nonce STA Nonce AP MAC Addr STA MAC Addr)3. Pairwise Transient Key –Collection of operational keys:
PTK = KCK KEK TK (bits 0-383)
–Key Confirmation Key (KCK bits 0-127) –used to bind PMK to the AP, STA; used to prove possession of the PMK
–Key Encryption Key (KEK bits 128-255) –used to distribute Group Transient Key (GTK)
–Temporal Key (TK bits 256-383) –used to secure data traffic and actually encrypt data with CCMP algorithm in Your case.Good luck!
Vertigo Generate x509 public key certificate.
Among the options you'll see for activating wireless encryption, 128-bit WEP is a safe bet. Older 40 or 64-bit WEP offers inadequate protection.